In this post, we will discuss troubleshooting OEM LDAP authentication issue. Due to various reasons, you may see sometimes the OEM users (LDAP users) getting Authentication failures. Well there could be various reasons for the authentication failures. We need to see how can we enable the tracing/debug to populate the detailed error messages in logs. The procedure is also explained in the Oracle Document.
Our troubleshooting started after users compaining about the authentication issues. We narrowed it with various testings/accessing other enterprise applications that the issue is only with the OEM. Now we have started our focus on troubleshooting authentication issue.
Check1 :
Check if the issue is with all the users ( Local and External ). If the issue is only with the External users(LDAP users), the primary focus of this post, Please proceed with the troubleshooting.
Knowing that the issue is only with the LDAP users, We focussed looking around the external ldap system. In our case, we are using Microsoft Active Directory to authenticate users to OEM.
Check2:
Check if the service account used to integrate for authentication is locked. The security/identity team in your Organization should be able to help you if the accout is locked or not. If the account is locked, Please have this account unlocked it. Verify if the issue is resolved. But if the issue is not with the account locked, proceed to the next step to continue troubleshooting ….
Check3:
If the issue is not with the account locked, try enabling the Weblogic Debug/Tracing as described below ……
From the WebLogic Server Console, enable logging, set the WebLogic debug log level and then the enable the debug flag.
- Navigate to Environment->Servers->EMGC_OMS1 and choose the Logging tab.
- Under Rotation, set the file rotation size to 64000.
- Expand Advanced.
- Under Message destinations(s) (Log file: region) set the Severity level to Trace.
- Navigate to the Environment->Servers->EMGC_OMS1 and choose the Debug tab.
- Check WebLogic->security->atn->DebugSecurityAtn.
- Click Save.
Now these settings will create a logfile ldap_trace.logATN. This file ldap_trace.logATN is located at $OMS_HOME/../../gc_inst/user_projects/domains/GCDomain
Following log messages are populated when we try to access the OEM using LDAP user accounts….
[oracle@askmoem12c GCDomain]$ tail -f ldap_trace.logATN
17:31:47.729 ldc=6 Connected to ldaps://adauth.askmlabs.com:389
17:31:47.730 ldc=6 op=227 BindRequest {version=3, name=CN=oem.service,OU=Users,OU=Accounts,DC=askmlabs,DC=com, authentication=********}
17:31:47.732 ldc=6 op=227 BindResponse {resultCode=49, errorMessage=80090308: LdapErr: DSID-0C09042F, comment: AcceptSecurityContext error, data 532, v2580}
17:32:30.334 ldc=7 Connected to ldaps://adauth.askmlabs.com:389
17:32:30.334 ldc=7 op=228 BindRequest {version=3, name=CN=oem.service,OU=Users,OU=Accounts,DC=askmlabs,DC=com, authentication=********}
17:32:30.336 ldc=7 op=228 BindResponse {resultCode=49, errorMessage=80090308: LdapErr: DSID-0C09042F, comment: AcceptSecurityContext error, data 532, v2580}
17:35:00.485 ldc=8 Connected to ldaps://adauth.askmlabs.com:389
17:35:00.485 ldc=8 op=229 BindRequest {version=3, name=CN=oem.service,OU=Users,OU=Accounts,DC=askmlabs,DC=com, authentication=********}
17:35:00.487 ldc=8 op=229 BindResponse {resultCode=49, errorMessage=80090308: LdapErr: DSID-0C09042F, comment: AcceptSecurityContext error, data 532, v2580}
17:37:06.171 ldc=9 Connected to ldaps://adauth.askmlabs.com:389
17:37:06.171 ldc=9 op=230 BindRequest {version=3, name=CN=oem.service,OU=Users,OU=Accounts,DC=askmlabs,DC=com, authentication=********}
17:37:06.174 ldc=9 op=230 BindResponse {resultCode=49, errorMessage=80090308: LdapErr: DSID-0C09042F, comment: AcceptSecurityContext error, data 532, v2580}
17:39:45.033 ldc=10 Connected to ldaps://adauth.askmlabs.com:389
17:39:45.033 ldc=10 op=231 BindRequest {version=3, name=CN=oem.service,OU=Users,OU=Accounts,DC=askmlabs,DC=com, authentication=********}
17:39:45.035 ldc=10 op=231 BindResponse {resultCode=49, errorMessage=80090308: LdapErr: DSID-0C09042F, comment: AcceptSecurityContext error, data 52e, v2580}
17:47:17.121 ldc=2 Connected to ldaps://adauth.askmlabs.com:389
17:47:17.122 ldc=2 op=223 BindRequest {version=3, name=CN=oem.service,OU=Users,OU=Accounts,DC=askmlabs,DC=com, authentication=********}
17:47:17.124 ldc=2 op=223 BindResponse {resultCode=49, errorMessage=80090308: LdapErr: DSID-0C09042F, comment: AcceptSecurityContext error, data 532, v2580}
^C
From the above error messages, the “resultCode=49” indicates that the bad password is used. Now we understand that the issue is to deal with the service account password. We changed the service account oem.service password and then updated the password in weblogic console as shown below.
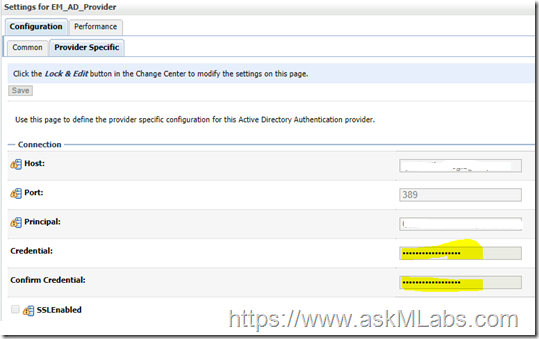
Follow the navigation to update the password ….
Domain - > Environment - > Security Realms - > myrealm - > providers
Save the password. And then activate the changes.
Ideally we don’t need to bounce the services to take these changes effect. But if you could offer the bounce, please bounce the complete OEM services.
Hope this information helps….







+ comments + 1 comments
Many applicants find it difficult to express their goals convincingly in admission essays. Professional assistance with writing a admission essay helps structure ideas clearly and present a strong personal statement. Expert writers ensure originality, proper tone, and clarity, making the essay impactful. This support helps applicants approach the admission process with confidence.
Post a Comment
Thank you for visiting our site and leaving your valuable comment.